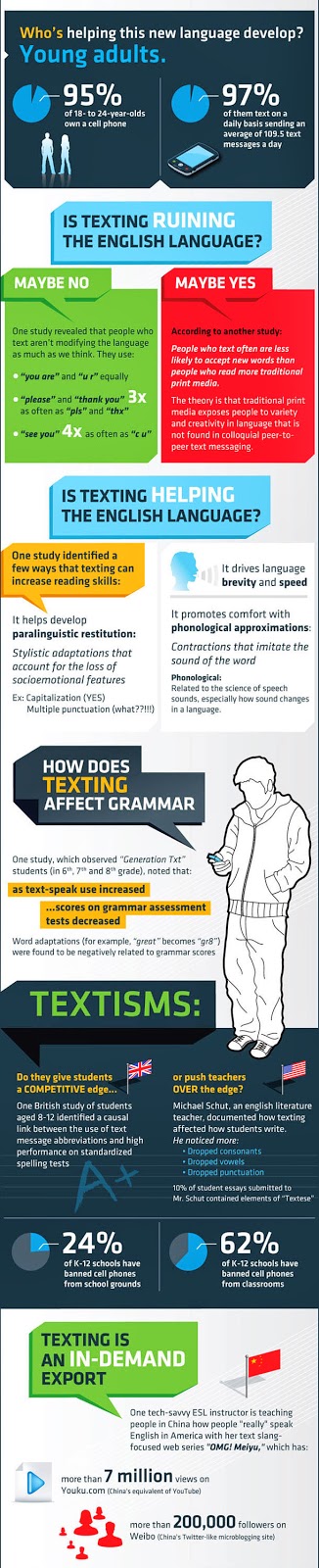
In the list of today we have very special personalities they were not heroes or champions but they are famous enough for their works such that the whole world wants to know about. They did the most offensive crimes the coolest way just by sitting in front of their Personal Computer. They were the hackers of all time who had the capability to stroll in the United States safest servers and retrieve as much information as they require. The list of top ten starts here;
10. John T. Draper
John T. Draper a United States Air Force trained personnel born in the year 1944, Draper due to his professional abilities and techniques learned became a renowned phone phreak and an iconic body in the world of computer programming, the skill was obtained while working as an engineer for National Semiconductor when he witnessed two blind kids using a modified toy shriek from a cereal box to make free phone calls through the payphone system. Using the mantle Captain Crunch, Draper popularized the use of the shriek and a host of other phreaking methods. Although his crimes are not extravagant, his lasting effect on the computing world is.
9. Kevin Mitnick
Kecin Mitnick is the greatest hacker of all time due to his brilliance and luminosity his crimes never popped up in front of Police and FBI, he suffered very less imprisonment not more than six years. He was the only one the FBI even labeled him “the most wanted computer criminal in United States history.”
8. Adrian Lamo
Adrian Lamo also known as “homeless hacker”, because of the fact he used Internet cafes, libraries, and Kinko’s, to hack during the day, and squatted in deserted buildings at night. It is only his immeasurable skills and achievements who brought him to this fame and respect although at a later stage. Adrian Lamo is now a day’s high-profile public speaker and an award-winning journalist. He used his hacking techniques and expertise to exploit different major companies like Microsoft and The New York Times.
7. Sven Jaschan
Seventeen years old German Jaschan built two viruses Sasser and Netsky and unleashed them on the Internet. Those two viruses posed heavy damage to Windows exposing the defects and related issues with the best selling operating system. Not only the Microsoft observed heavy and colossal loss but the effect of these was much more dramatic than we could think. It disabled the networks of businesses throughout the world, which even included shutting down airlines and entire satellite systems. Well these related issues have posed a challenge to search for better windows security systems and etc.
6. Dmitri Galushkevich
In the year 2007, Estonia and Russia sheltered up in a clash over the removal of Soviet era statues. Therefore, when Estonia suffered the worst hacker attack in their history at that same time, it was easy to blame the Russians. The attack overloaded servers throughout the country shutting down all forms of commerce. In the end, the culprit was Galushkevich, a 20-year old ethnic Russian living in Estonia. Some still suggest that Galushkevich was a Russian pawn, but there was never any evidence to support that claim.
5. Robert Tappan Morris
Robert Morris was the son of previous NSA scientist also famous for the name of Black Hat hacker when he unleashed the first computer worm on the Internet, a well known professor at MIT, United States of America. To this day, Morris asserts that he built the Morris worm simply to evaluate the size of the Internet. However, it was clear that he had other plans for this excessively replicating worm that brought the Internet to its knees. Damage estimates from the worm’s crash differ greatly, as do the real number of systems and individual computers that were affected. But the numbers applied to Morris are concrete: After some plea bargaining, he was sentenced in December 1990 to three years’ probation and fined $10,000 (about $17,000 in today’s money).
4. Kevin Poulsen
Kevin Poulsen also Known as Dark Dante and tagged as the “the Hannibal Lector of computer crime” by law enforcement. Kevin Poulsen made some of the most noticeable hacks in history. The most famous one included winning a Porsche from KIIS-FM radio station by taking over their phone lines, and even shutting down the phone lines of the America’s Most Wanted television program when he was the feature. Among other things, Poulsen reactivated old Yellow Page accompany telephone numbers for an acquaintance that then ran a virtual agency. When the FBI started chasing Poulsen, he went underground as a renegade. When he was featured on NBC’s unanswered Mysteries, the show’s 1-800 telephone lines mysteriously crashed. He was finally arrested in February, 1995.
3. Raphael Gray
Raphael was arrested by the FBI at his home on the 23 March 2000. Police and FBI agents arrived in the morning. It was supposed that he had intruded into nine e-commerce websites in Britain, America, Canada, Thailand and Japan and taken details of some 26,000 credit card numbers and disclosed some of the credit card information on the Internet. Raphael, who was only 18 at the time give details to the police and FBI when he was dialogued that he had been worried for sometime at the intrinsic security weakness in one exacting create of software called “Microsoft Internet Information Server”. This intrinsic flaw enabled distant users to entrée information stored on computers using this software. Raphael explained he had contacted a number of e-commerce sites using this software and pointed out the security weakness but they had ignored him, and he had also contacted Bill Gates, the Microsoft Chief who again ignored him.
2. Jonathan James
Perhaps James’/c0mrade’s greatest claim to fame is that at 16, he became the first juvenile hacker sent to prison. However, his offenses were legitimate and serious. His highest-profile crime occurred when he compromised NASA computers and stole software worth $1.7 million. Another major offense came when he installed backdoor access into the servers of the Defense Threat Reduction Agency, which is responsible for monitoring biological, chemical, conventional, nuclear, and special weapon threats to the U.S.
1. Gary McKinnon
Gary McKinnon, the Britain blamed of hacking Pentagon and NASA computer networks, faces an increasingly antagonistic weather on cyber security in the US if his exile is approved this week. He trespassed the networks of the U.S. Army, Air Force, Department of Defense, NASA, and Navy. The thing he required was the evidences of aliens and their space shuttle or spacecraft, which he could use to resolve the global energy disaster. McKinnon’s case is still continuing and his lawyers assert that he is worthy of special deliberation because he is bothered with Asperger’s Syndrome.
This post is This post sponsored by: